Search
Items tagged with: infosec
On the Internet, everyone is automatically signed up for a free pen test. You just may or may not get the results and findings.
Looks like Corporate #infosec has made it's choice.
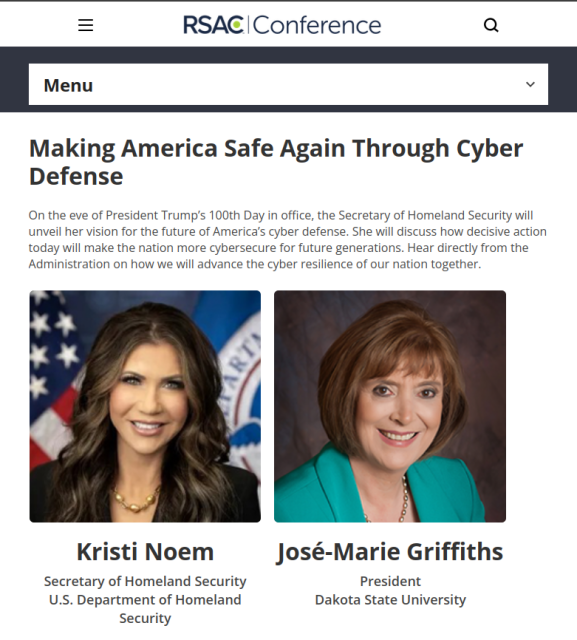
#RSAC is filled with talks embracing AI and making it "secure".
And they invited and encouraged the Trump regime to spread its disinformation - fully sanctioned and encouraged by the conference leadership(and by conference attendees who laughed at the regime's jokes and lies and issued no challenges or stands during the talk).
With the ostracization of #ChrisKrebs by industry and the full embrace of Kristi Noem as a speaker, this was the moment that infosec made its bed.
Y'all lie in it now.
Microsoft Authenticator needs me to validate with Authenticator in order to log in with Authenticator to use it to authenticate another app with Authenticator.
Here is the app telling me to open itself to validate itself with itself.
"In response to a request from USA TODAY, the labor board stated it had no comment but shared a memo to staff dated April 16, that said prior to April 15 the agency 'had no official contact with any DOGE personnel'."
USA Today: Is DOGE risking the government's cybersecurity? Some have lost their jobs to block them https://www.usatoday.com/story/news/politics/2025/04/28/doge-database-quest-risking-government-cybersecurity-musk/83144274007/ @USAToday #cybersecurity #infosec #Musk @briankrebs

Is DOGE risking the government's cybersecurity? Some have lost their jobs to block them.
DOGE workers are scrutinizing federal databases to cut spending, but does that sweeping access to private information risk a data breach?, USA TODAY (USA TODAY)
I love it when employers install creepware #surveillance nonsense because they have zero respect for their employees, and end up publishing 21 million internal screenshots to the web instead, leaking their most sensitive information.
Very nice, no issues.
#cybersecurity #infosec #assholeBoss
“Employee monitoring app leaks 21 million screenshots in real time”
https://cybernews.com/security/employee-monitoring-app-leaks-millions-screenshots/
CVEs are published by CNAs and the process of submitting CVEs is decentralized.
CVEs are available here: #infosec
https://github.com/CVEProject/cvelistV5

GitHub - CVEProject/cvelistV5: CVE cache of the official CVE List in CVE JSON 5 format
CVE cache of the official CVE List in CVE JSON 5 format - CVEProject/cvelistV5GitHub
Sharing for our Federal employee friends, please REPOST and show up if you can:
ACTION REQUEST
Hi everyone - today USAID staff in Washington received word that they can go into USAID headquarters at the Ronald Reagan building to retrieve their personal belongings. The entire Washington-based staff have two days, this Thursday and Friday, in one-hour windows by bureau, and in 15-minute increments, per person. No boxes or packing materials will be provided. There are staff who have worked at the RRB for 20-30 years , and it is the "mother ship" for most of us. This will be an extremely emotional two days.
So, we would like to encourage anyone who is in the DMV area, and able to, please join us at RRB to "clap out" staff, with signs of support. If you're able to bring extra packing materials and / or drinks and snacks, please do. We want to show these people how you treat public servants who have given their lives to the important work we do.
THURSDAY 7:30am - 6:00pm
FRIDAY 7:30am - 3:30pm
USAID
Ronald Reagan Building
1300 Pennsylvania Ave NW
Washington D.C.
There is public parking in the RRB garage, and the closest metros are Metro Center (red line) and Federal Triangle (orange/blue). If you are planning to park in the garage, please make sure you have a government issued ID (driver's license).
#government #USAID #organize #MutualAid #tech #infosec #politics #USpol #uspolitics
Update Signal and pay attention when joining groups:
https://www.wired.com/story/russia-signal-qr-code-phishing-attack/
👉 No, Signal has not been compromised
👉 No, Signal encryption has not been broken
👉 No, there is no back-door in Signal
You should continue using Signal. The update is responding to a sophisticated, state-level attack targeting specific groups.
Unless you are a high-value target, you are almost certainly never going to see this in the wild.
If you know you are a high-value target, ask your support.

A Signal Update Fends Off a Phishing Technique Used in Russian Espionage
Google warns that hackers tied to Russia are tricking Ukrainian soldiers with fake QR codes for Signal group invites that let spies steal their messages. Signal has pushed out new safeguards.Andy Greenberg (WIRED)
insider threats just got real. Anyone have "coup d'etat" in their risk matrix?
I notice that the preview is blocked for my instance.
Not that I need to go there anyway, because I know the story. The credit reporting agencies are all a scam to collect updated PII from people that get magically get awarded 2 free years of credit monitoring via some class action lawsuit you were not aware of in the first place.
If you get an offer for this free credit monitoring, throw it in the trash.
It is not free. They will sell your PII.
There's a "Signal deanonymized" thing going around:
https://gist.github.com/hackermondev/45a3cdfa52246f1d1201c1e8cdef6117
Stay calm. Deep breaths.
👉 while this is a real consideration, the only thing the attacker gets from this is a very rough (kilometers or tens of kilometers radius) location
👉 other communication platforms that use any kind of caching CDN to deliver attachments are just as affected
👉 you almost certainly should continue to use Signal, unless you specifically know that this is a big problem for you.

Unique 0-click deanonymization attack targeting Signal, Discord and hundreds of platform
Unique 0-click deanonymization attack targeting Signal, Discord and hundreds of platform - research.mdGist
Are you on Signal or Wire yet? Go do that. Gently move your friends/fam over to one of the platforms. Set disappearing messages on both sides of the conversation. Be careful what you say in group chats, know who you trust, and who are your Vault people. For REAL sensitive stuff, in-person, no phones.
Normalize going places without your phones, leave them at home now and again to establish a pattern.
Please understand anyone who works in advocacy, healthcare (esp reproductive rights/women's healthcare), journalists, some gov officials, marginalized groups will likely be targeted.
If this doesn't fit your threat model/risk profile, you know someone who will be impacted by oversight, surveillance or someone snitching
#tech #infosec #security #safety #privacy #security #community #education
Such a great episode of @riskybiz podcast with @briankrebs
https://castro.fm/episode/aGUI3L

Risky Business: Wide World of Cyber: SentinelOne's Chris Krebs on Chinese cyber operations (50m)
In this edition of the Wild World of Cyber podcast Patrick Gray sits down with SentinelOne’s Chief Intelligence and Public Policy Officer Chris Krebs to talk all about Chinese cyber operations.castro.fm
4/4
💯 Don’t miss out on this incredible opportunity!
🔗 Help us spread the word!
#GoTALER #onlinepayment #tech #technology #banking #finance #onlineshopping #freesoftware #openSource #developer #programming #privacy #DigitalRights #PublicCode #cybersecurity #infosec
@nlnet @ps @EC_NGI @Taler @glsbank @leoo @oec @EUCommission @EU_Commission @TUEindhoven @NGIZero @ngi @NGICommons
Who mentioned cars?
Researchers find security flaws in Skoda cars that may let hackers remotely track them https://techcrunch.com/2024/12/12/researchers-find-security-flaws-in-skoda-cars-that-may-let-hackers-remotely-track-them/ @TechCrunch @carlypage @briankrebs #cybersecurity #infosec #privacy

Researchers find security flaws in Skoda cars that may let hackers remotely track them | TechCrunch
Security researchers have discovered multiple vulnerabilities in the infotainment units used in some Skoda cars that could allow malicious actors toCarly Page (TechCrunch)
#curl 8.11.1 has been released. It includes a fix to #CVE_2024_11053 - a #vulnerability I discovered.
It is a logic flaw in the way curl parses .netrc file. In certain situations, the configured password can be sent to a incorrect host. Luckily the affected configurations should be quite rare and thus the situation is unlikely to occur often.
The issue has existed in the curl source code for almost twenty-five years.
• https://curl.se/docs/CVE-2024-11053.html
• https://hackerone.com/reports/2829063
No AI tools were used in discovering or reporting the vulnerability.
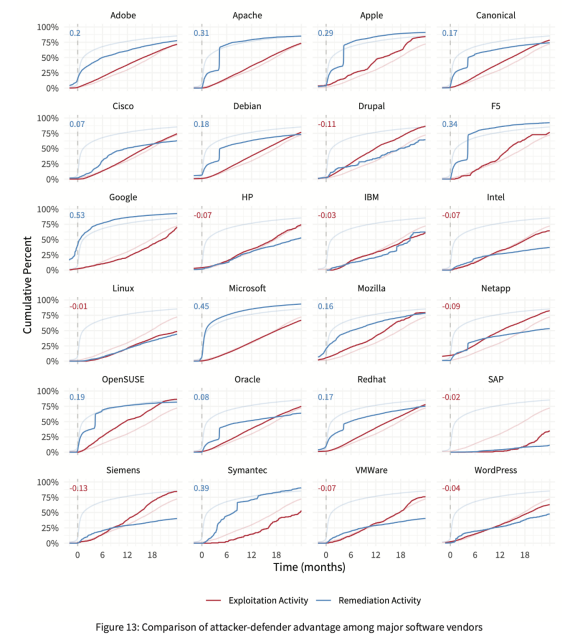
I'm fascinated by the concept of measuring attacker-defender advantage in software, devices, and even entire IT environments. What do I mean by "attacker-defender advantage?" Lemme sum up and then share a chart.
Let's say you could measure the speed at which defenders remediate various types of security vulnerabilities across all relevant assets. Then say you could detect and measure the speed at which attackers find/exploit those vulnerable assets across the target population of organizations using them. Finally, plot those curves (across time and assets) to see the delta between them and derive a measure of relative advantage for attackers and defenders. That relative value is what I mean by attacker-defender advantage.
Since a picture is worth a thousand words, here's a visual example of the concept. The blue line represents defenders, measuring the speed of remediation. Red measures how attacker exploitation activity spreads across the target population. When the blue line is on top, defenders have a relative advantage (remediating faster than attackers are attempting to exploit new targets). When red's on top, the opposite is true. The delta between the lines corresponds to the relative degree of advantage (also expressed by the number in the upper left).
This chart comes from prior Cyentia Institute research in which we were able to combine datasets from two different partners (with their permission). Unfortunately, those datasets/partners are no longer available to further explore this concept - but maybe this post will inspire new partnerships and opportunities!
Any surprises in the attacker-defender advantage results depicted in the chart? Has anyone measured this or something similar?
#cybersecurity #vulnerabilities #cyberattacks #infosec #exploitation
Hey, have you downloaded #Graylog 6.1 yet? We caught up with Adam "Abe" Abernethy and Rich Murphy at the recent OpenSearch Project conference to find out what's new and exciting in this monster of a release. 🐲 Hear what they have to say, plus check out this awesome overview video via Ethan C. Keaton on YouTube! 📺👇
https://www.youtube.com/watch?v=yfKbBYYB66Q&list=PLZrCvztUUBfvh0TQMjiAFbotitDVsCdC9 #cybersecurity #infosec #logmanagement #APIsecurity #security
- YouTube
Auf YouTube findest du die angesagtesten Videos und Tracks. Außerdem kannst du eigene Inhalte hochladen und mit Freunden oder gleich der ganzen Welt teilen.www.youtube.com
For those who don't know (which is most of you), this project has been the intense focus of my work, taking up a huge amount of my time, energy, and investigative effort for the past 14 months - while still helping others at Sophos publish their research; running an election campaign where I was a candidate for school board; speaking at Blue Hat, Defcon, Saintcon, Virus Bulletin and other conferences; guest lecturing to classes at CU Boulder; volunteering my time canvassing for political candidates; serving as a docent at the @mediaarchaeologylab and starting up the Elect More Hackers organization.
Whew. It's actually kind of daunting just to read that. I also sometimes sleep and eat.
@SophosXOps has been, at its core, an institution that values radical transparency, and this story (and the earlier research investigations into the Operation Pacific Rim threat actors and incidents) demonstrates Sophos' commitment to truth and journalistic integrity, following a story wherever it leads.
I hope our publication today starts a larger conversation and collaboration within the cybersecurity industry - inside and outside the Cyber Threat Alliance, which Sophos actively supports and where I am proud to represent my employer - to work together to thwart the ambitions of nation-state threat actors such as the perpetrators of Operation Pacific Rim, in order to protect the privacy and safety of everyone, everywhere.
#PacificRim #OperationPacificRim #malware #china #hacking #hacks #infosec #firewalls #intrusiondetection
https://www.sophos.com/en-us/content/pacific-rim

Sophos' Pacific Rim: Defense Against Nation-state Hackers
Discover Sophos' Pacific Rim defense against nation-state / Chinese hackers Volt Typhoon, APT31, and APT41 targeting critical infrastructure.Sophos
I have a friend who is being harassed and threatened semi-anonymously via Facebook. She knows *who* it is, but Facebook and Police are characteristically being uselss.
I am kinda useless at this side of deanonymization, but does anyone have advice or resources for deanonymizing enough to get cops to move?
4/4 🚀 🚀 🚀
Don’t miss out on this incredible opportunity! #GoTALER #onlinepayment #tech #technology #banking #finance #onlineshopping #freesoftware #openSource #developer #programming #privacy #DigitalRights #PublicCode #cybersecurity #infosec
In der IT kann es schon mal stürmisch werden! 🌪 Ihr wollt Cyberkriminelle von der Party ausschließen? Hier verraten wir euch, wie ihr eure digitalen Fenster und Türen absichert: 👉 https://www.bsi.bund.de/dok/131400
Ihr habt noch einen? Wir freuen uns eure liebsten IT-Flachwitze in den Kommentaren! 😜
#DeutschlandDigitalSicherBSI #IT #ITSicherheit #Sicherheit #CyberSecurity #ITSecurity #InfoSec #CyberCrime
As I'm attempting to do a write up on National Public Data breach, it keeps devolving. So I'm going to link to all the things, tips, sites I have used and hopefully that helps people navigate next steps. Please consider freezing your credit. It's not a cure-all but it can help.
Krebs has a good write up on it to start https://krebsonsecurity.com/2024/08/national-public-data-published-its-own-passwords/
I'll post all the things I've done as well. Should have blog up in in a few hours.

National Public Data Published Its Own Passwords
New details are emerging about a breach at National Public Data (NPD), a consumer data broker that recently spilled hundreds of millions of Americans' Social Security Numbers, addresses, and phone numbers online.krebsonsecurity.com
Important update from @briankrebs regarding the NPD breach:
https://krebsonsecurity.com/2024/08/national-public-data-published-its-own-passwords/
I hope quality reporting like this will foster a healthy discussion about how and to whom we entrust PII, but I won't be holding my breath.
In the article, Krebs provides links to sites that check
if your PII was exposed in this breach.
#infosec #cybersecurity #breach #pii

National Public Data Published Its Own Passwords
New details are emerging about a breach at National Public Data (NPD), a consumer data broker that recently spilled hundreds of millions of Americans' Social Security Numbers, addresses, and phone numbers online.krebsonsecurity.com

Jaw Dropping DNS Attack Vector Heavily Exploited in the Wild
Learn about the insidious DNS attack vector that threat actors are using to hijack domains from major brands, government institutions, and other organizations, large and small. Find out how to determine whether your domain name is at risk.Infoblox Threat Intel (Infoblox Blog)